In simple words, the PKI software solution allows companies to gain high-level information confidentiality through strong data encryption giving high-level confidence.
Let’s understand the PKI software solution with an example.
Rahul wants to send an official secured email to Anita. Anita has a private key and a Public key. These keys are unique from one another.
Rahul will request Anita for her public key. You can distribute your public key to anyone who wants to send a message. Further, it also means the key is not a secret and does not require any special protection.
Anita now sends the key to Rahul, who uses it to encrypt the message and sends it to Anita. Now, any message encrypted with a public key can only be decrypted with a private key. So Anita uses her private key to decrypt Rahul’s message.
This is great for confidentiality!
In the modern digital world, we see everything is getting easier and comfortable. But things are easier because a thousand technologies work together to make it happen. One such technology is Public Key Infrastructure, shortly PKI. This technology is used for authenticating users and devices. This includes signing documents digitally, where more than one trusted parties certify that a particular cryptographic key is owned by a specific user or device. The key can then serve as an identity for the user across digital networks.
Additionally, keys aren’t exclusive to users or devices, as it can also be a program, process, manufacturer, component or something else. And PKI works towards associating the key with an entity securely.
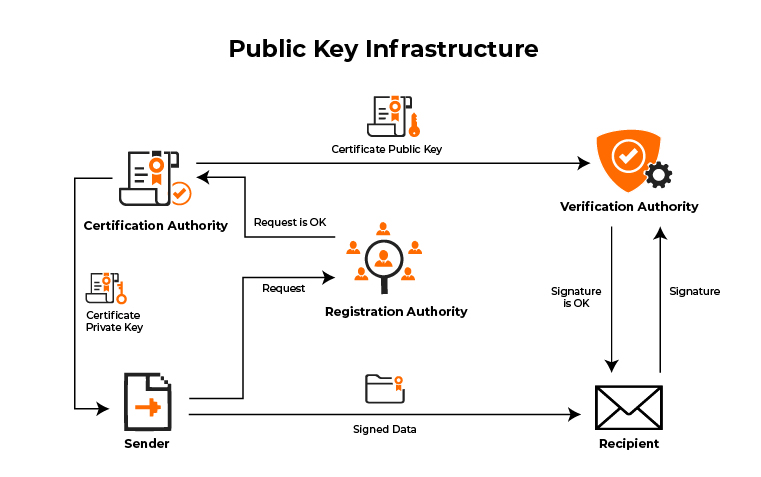
The trusted parties that sign the digital documents are certificate authority (CA), who also own a cryptographic key used for signing documents. These signed documents are called certificates.
3 main vital components of PKI
PKI software solutions incorporate few components on a protected framework and protect the identities and pieces of private and confidential information in activities where a digital key is involved. For example, SSL signatures, smart card logins, encrypted documents, etc. These components play the heart and soul in securing digital information and transactions. Let’s take a look at the 3 main components deeply to understand the PKIs contribution to security.
- Digital Certificates
PKI is nothing without a digital certificate, just like a driver is nothing with a driver’s license. Well, not legally, at least. A digital certificate serves as an identity for websites and organisations. When two machines communicate, the connection is secure because PKI uses digital certificates to verify the identity. Devices can get these certificates by creating their own, if for internal communications. But in case you want certificates for commercial sites, you can use a third-party issuer, called Certificate Authority. With a licensed Certificate Authority, you can quickly get digital certificates in India. - Certificate Authority
A Certificate Authority (CA) authenticates the users’ digital identities, including individuals, computers or servers. CA will work towards identifying falsified entities while managing the validity of a digital certificate within the system. The issuing and accountability of certificates work similarly to a driving license. Just like a government issues you a license, and your identity is trusted across other purposes, Certificate Authorities give organisations a digital certificate to trust the devices. A similar process is used for code signing when it verifies programs and downloads. - Registration Authority
Registration Authority uses authorisation by Certificate Authority to issue digital certificates to users or organisations on a case-by-case basis. Certificate Authority and Registration Authority stores all the certificates that are either requested, received or revoked by them. The storing is done in an encrypted certificate database. PKI can implement various functions, and it can also be customised to support other functions like the following:
- RA might be customised to verify an individual’s information and details as part of the initialisation process, for example, verifying the physical presence and other identifications.
- Generate materials like keys for the end-user
- Perform certain functions like key or certificate life cycle
Challenges Businesses are Facing
Sure PKI has been helping businesses thrive where they can work on the security models according to their specific requirements. Yet enterprises face challenges in management, especially in defining, maintaining, securing, and managing the PKI.
- There is a chance that a deceptive certificate might be issued in case of the theft of CA signing private keys.
- Even accepting that the keys are not compromised, there’s a chance that weak management and controls will lead to a CA’s misuses.
Advantages of PKI Certificate
PKI Solution Provider in Odisha provides authentication that uses digital certificates. The protection of electronic data gets a considerable boost with PKI solutions. Digital certificates are trusted because the attempt to falsify is next to impossible as they are profoundly detailed and unique for each user or device or entity.
A digital certificate has details incorporated in them. After they issue a unique digital certificate to an entity, all the pieces go through an in-depth process, including PKI authentication and authorisation. Some security processes are time stamping, registration details, validation, and other information required to ensure both entities’ privacy.
Providing PKI Services
Public key infrastructure plays a vital role in securing digital communications. To provide a secure connection across the wire, a PKI works towards providing four primary services:
- Confidentiality: You have the liberty to choose who will read your data that will include keeping details to yourself or sending to someone, particularly to whom you want to read.
- Integrity: They do not tamper To ensure that whatever data you send with, and that’s exactly what the other party receives.
- Authentication: With this service, you know that whatever you are sending to a person is read by that person only and not received by their device by reading by a different person.
Non-repudiation: To ensure that you can prove the contents and details of data to a third party.
Securing Information Online with PKI solutions
Public key infrastructure in information security has shown enough promises so far. While secure authentication fails us time and again with failing to handle security breaches, Certificate Authority and Registration Authority is something businesses like to invest in. We can invest a lot of trusts while investing in cloud-based PKI solutions.
PKI for Email Security
Just like PKI solutions works wonders with securing web traffic, it works similarly with securing the email. Without a secure connection and encryption, your overflowing data on the internet has high chances of getting intercepted and read. A sender is hard to be trusted who claims to be existing with real details unless you have a way that you can use to authenticate their identity. Since most of the necessary infrastructure is built into web browsers and servers, establishing PKI for web traffic is tough. But since email is accessed through heterogeneous clients, things get a bit difficult.
Final Decision on Getting PKI
PKI is not a question of whether you should invest, but an answer to all your security issues. It has worked towards securing all the aspects of the digital world by protecting sensitive information and data, not forgetting securing our connections and communications. The number of connections of devices is growing every day and the demand for security grows with it.
Especially with large enterprises, introducing PKI is becoming very critical. Managing millions of digital certificates with PKI programs’ best practices is a challenge faced by many enterprises today.
Our Take
The setup process of PKI involves the configuration of all the PKI components and an ongoing maintenance and storage requirement to protect in case of a physical breach. Security around PKI will need robust maintenance because if the public key or root CA is stolen or say tempered with, every certificate comes in risk which will need replacing.
When it comes down to it, we rely on public PKI infrastructure every time- while shopping, banking, filling out official forms, etc. These all include placing our most precious and sensitive information. The threats will always exist, yet we do trust the companies to protect our data like they claim to.
If you wish to opt for a cloud-based PKI solution and are looking for PKI Solution Provider Odisha, connect with NTSPL. NTPSL is a renowned name for providing public key infrastructure in information security services.